Key takeaways
- Risk management is the process of identifying, assessing, mitigating, transfering, and monitoring cybersecurity threats
- Cyber risks include malware, ransomware, phishing attacks, social engineering, employee threats, and cloud vulnerabilities
- Understand the importantance of cyber insurance to assist both with incident response, first-party costs, and third-party liabiities
- Cyber security is an ongoing commitment that requires continuous monitoring and improvement to stay ahead of evolving threats
What is cyber risk management?
Cyber risk management is the process which businesses identify, assess, mitigate, transfer and monitor risks associated with cybersecurity threats. Failure to adequately manage your cyber security, could lead to compensation claims seeking financial damages, regulatory fines, operational disruption, extortion attempts, reputational damage, and loss of customers.
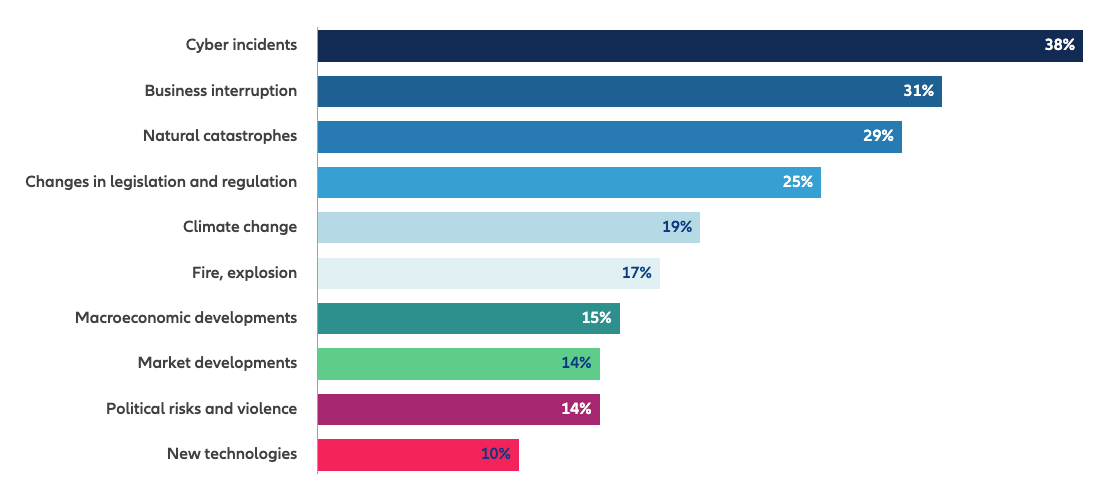
Allianz Insurance undertook a survey of the major business risks in 2025, and cyber incidents were identified as the most concerning from the respondents.
Understanding cybersecurity risks
Businesses today face a wide range of cybersecurity risks, including malware, ransomware, phishing attacks, social engineering, employee threats, and vulnerabilities associated with cloud services.
Ransomware has emerged as one of the most damaging cybersecurity threats, with companies facing significant financial losses and operational disruptions when malicious actors encrypt data and demand payment. Whereas increasing reliance on hosted services means businesses increasingly rely upon these services without always implementing robust security practices and ensuring adequate cyber insurance for third-party suppliers. Whilst phishing and social engineering attacks which exploit human vulnerabilities, have led to significant breaches and cybercrimes even when cybersecurity controls have been robust.
Cyber risk management checklist
Risk Identification, Assessment and Monitoring
• Vulnerability scans
• Penetration testing
• Identify roles and responsibilities
• Risk matrix and modelling
• Regular reviews and reporting
Risk Mitigation and Business Continuity
• Firewalls and intrusion detection systems
• Endpoint protection and antivirus
• Multi-factor authentication (MFA)
• Third party insurance requirements under contract
• Data encryption (in transit and at rest)
• Regular software updates and patch management
• Security Information and Event Management (SIEM)
• Clearly defined cybersecurity policies
• Employee cybersecurity training
• Restricted physical access to critical IT infrastructure
• Secure management of mobile devices and equipment disposal practices
• Incident response planning
• Maintain regular and secure backups
• Periodically test backup capabilities
• Provide access to Incident response services
• Financial protection against 3rd party liabilities and legal costs
• Cover for ransom demands
• Cover the financial interruption to the business
• Cover for incurred costs and expenses
• Cover for regulator fines and penalties
Cyber risk management process
Risk Identification
Identifying potential cyber threats and vulnerabilities is the first step in effective cyber risk management. This involves conducting vulnerability scans and penetration testing to identify weaknesses within systems and software. However, it should also consider the human element to identify the risks posed by employees. Regular and thorough risk identification helps business proactively prevent cybersecurity incidents before they occur.
Risk Assessment
Following identification, businesses must assess and evaluate each risk by considering its potential impact and likelihood. Risk matrices are commonly employed to prioritise threats, allowing for targeted and efficient allocation of resources. Risk assessments should consider both technical vulnerabilities and human factors, such as employee behaviour and culture.
Risk Mitigation
To mitigate cyber risks effectively, businesses must adopt robust strategies, including multi-factor authentication (MFA), endpoint security solutions, regular cybersecurity awareness training, secure data backups, encryption, and strict access management policies. Employee training, in particular, plays a critical role, as human error remains a primary cause of cybersecurity breaches.
Risk Transfer
Cyber insurance is a critical component of cyber risk management because malicious actors, evolving cyber threats, and employees can potentially bypass your cyber security controls. Cyber cover can provide protection against financial losses, provide access to
incident responses services, and assist with getting your business up and running as soon as possible.
Risk Monitoring
Continuous monitoring and frequent reviews are vital components of cyber risk management. Real-time monitoring solutions, coupled with comprehensive threat intelligence, allow businesses to quickly detect and respond to evolving threats. Regular cybersecurity audits further ensure that systems and procedures remain effective and aligned with best practices.
Legal and regulatory landscape
Businesses can face significant fines and legal liabilities following a cyber attack or data breach. For example, violations of data protection laws which protects
personally identifiable information (UK GDPR and Data Protection Act 2018) can mean the Information Commissioner’s Office (ICO) impose fines of up to £17.5 million or 4% of annual global turnover, whichever is higher.
Whereas customers or third parties which have been impacted by a data breach or cyber attack may seek damages. This could mean a compensatory claim for financial losses arising from: loss of revenue; fraud; loss of intellectual property or sensitive business information; costs and expenses incurred, such as ransom payments, forensic investigations, data restoration; reputational damage; emotional distress; and identity theft fraud.
Claims of negligence or breach of contract can lead to costly legal expenses and damages awarded. Tech companies can seek to mitigate these risks with
technology E&O insurance, which provides protection against liability claims arising from the performance of their services.
Cybersecurity risk management frameworks
Risk management frameworks such as ISO 27001 and the UK
Cyber Essentials certification offer risk management frameworks to cybersecurity. ISO 27001 emphasises information security management and establishes clear controls to protect sensitive data. Whereas Cyber Essentials offers straightforward yet effective cybersecurity measures for small and medium enterprises (SMEs).
Implementing cyber risk management
Despite the increasing awareness of cybersecurity, businesses often make common mistakes that undermine their efforts. Many businesses focus primarily on external threats and overlook risks from employees, contractors, 3rd parties, or partners.
Employees unaware of cybersecurity best practices can unintentionally facilitate breaches or cybercrime through poor password management, insecure data handling, or susceptibility to phishing attacks.
Without clear incident response plans, businesses can experience prolonged downtime and increase the costs and expenses associated with a cyber incident. Additionally, relying solely on technology without addressing human and procedural factors creates gaps exploitable by cyber attackers.
Cyber risk management is an ongoing commitment that requires continuous monitoring, adaptation, and improvement to stay ahead of evolving threats. Risks posed from cyber criminals continue to evolve, therefore the measures employed may always be one step behind. Below we’ve identified some measures that are recommended:
Firewalls and Network Security
Firewalls serve as the frontline defence, monitoring and filtering incoming and outgoing network traffic based on predetermined security rules. Modern firewalls, including next-generation firewalls (NGFWs), offer advanced protection through intrusion detection and prevention systems (IDS/IPS), content filtering, and application-aware monitoring. Businesses should deploy firewalls at network perimeters, continuously update rules, and regularly review firewall logs to detect potential security incidents.
Endpoint Protection
Endpoints, including laptops, desktops, servers, and mobile devices, are frequent targets for cyber attackers. Implementing endpoint protection platforms (EPP) and endpoint detection and response (EDR) solutions helps businesses quickly detect, prevent, and respond to threats. Regularly updating antivirus software, managing patches, and implementing device encryption further strengthen endpoint security.
Secure Configuration
Misconfigurations are common vulnerabilities exploited by cybercriminals. Businesses should consistently apply security patches and software updates to address known vulnerabilities. Secure configurations also involve disabling unnecessary ports and services, removing default accounts, and implementing configuration baselines aligned with industry standards.
Data Encryption
Encryption is crucial for protecting sensitive information. Businesses should implement encryption both at rest (stored data on servers, laptops, and mobile devices) and in transit (using TLS/SSL protocols for data transfers). Strong encryption practices mitigate risks associated with data theft, unauthorised access, and interception during data transmission.
Identity and Access Management (IAM)
IAM systems manage user identities and permissions, ensuring employees have appropriate access aligned with their roles. Enforcing the principle of least privilege—granting minimal necessary permissions—prevents excessive access and reduces the potential damage from compromised accounts. Regular reviews of access rights help maintain security over time.
Multi-Factor Authentication (MFA)
MFA significantly enhances account security by requiring users to provide two or more verification factors before gaining access. Businesses should implement MFA across critical systems, particularly cloud services, email platforms, and remote access gateways, to reduce the risk of unauthorised access.
Password Management
Passwords remain fundamental in cybersecurity defences. Businesses must enforce strong, complex passwords or passphrases, educate employees on secure password practices, and utilise password managers to facilitate secure password management across applications and devices.
Cybersecurity Training
Employee awareness remains one of the most critical elements of cybersecurity. Regular training helps employees recognize phishing attempts, avoid social engineering traps, and follow secure data handling practices. Simulated phishing exercises further reinforce training and identify knowledge gaps.
Cyber Incident Response
Employees must understand how to respond swiftly and appropriately to cybersecurity incidents. Incident response training should detail procedures for reporting suspicious activities, escalating threats, and activating the incident response plan, minimising damage during incidents.
Physical Security
Protecting physical access to IT systems and sensitive data still remains essential. Businesses should restrict access to server rooms, networking equipment, and
data centres through locked facilities, access cards, with potential for biometric authentication, and surveillance systems. Additionally, secure disposal of sensitive physical documents and electronic media mitigates risks of data leakage.
Device Management
Mobile devices and remote endpoints pose significant cyber risk if unmanaged. Implementing strict mobile device management (MDM) policies, encrypting data on devices, ensuring remote wipe capabilities, and controlling device access helps maintain security for distributed workforces.
Cloud Security
As businesses increasingly rely on cloud services, maintaining cloud security becomes paramount. Companies must enforce secure cloud configurations, regularly audit cloud services, encrypt cloud-stored data, and manage access permissions meticulously. Leveraging cloud security posture management (CSPM) tools can automate continuous monitoring and compliance.
Supplier Risk Management
Cyber risk frequently arise from third-party technology suppliers. Businesses should perform cybersecurity assessments, clearly define cybersecurity expectations, request evidence of their cyber and professional indemnity insurance, and ensure these are contractually agreed and monitored.
Data Backup and Recovery
Regular, secure backups of critical data are essential for recovery after cyber incidents, such as ransomware attacks. Businesses should store backups offsite or in secure cloud locations and regularly test backup restoration processes to verify their effectiveness.
Business Continuity Planning
A robust business continuity plan outlines procedures for maintaining essential operations during cyber disruptions. Continuity planning should identify critical business functions, establish recovery priorities, define alternate work arrangements, and clearly communicate roles during incidents.
Cyber Insurance
Cyber insurance can provide financial protection and expert support to help recover from a cyberattack or data breach. It can provide the necessary financial resources to cover your legal liabilities, provide access to incident response services, pay ransomware demands, cover your loss of profits, forensic investigations, legal fees, public relations costs, customer notifications, and potential regulatory penalties.
Regular Audits and Reviews
Periodic cybersecurity audits and compliance reviews ensure controls remain effective, adapt to evolving threats, and adhere to industry standards. Audits should cover technical controls, policies, employee compliance, and regulatory requirements, providing critical feedback for continuous improvement.
Continuous Monitoring
Real-time monitoring solutions like Security Information and Event Management (SIEM) enable businesses to quickly detect, analyse, and respond to cyber threats. Continuous monitoring provides visibility into security events, anomalies, and vulnerabilities, enabling rapid detection and remediation.
Do we need a cyber risk management strategy?
Investing time and resource in cyber risk management is not only prudent but essential. With an increasing frequency and severity of cyber attacks and data breaches, no business is immune from ever-evolving digital threats.
Larger businesses will have more resource at their disposal, however small to medium sized businesses still need consider how best to identify, assess, mitigate, transfer, and monitor cybersecurity risks. Malicious actors and cybercriminals will target weaker companies with lessor controls no matter their size.
Businesses should take a proactive, continuous and holistic approach in dealing with cybersecurity threats. Insurance should not be viewed as a replacement for cybersecurity, because insurers will usually require
minimum cybersecurity controls to provide cover in the first instance.
